HPE6-A84 Aruba Certified Network Security Expert Written Exam exam dumps
questions are the best material for you to test all the related HP exam topics. By
using the HPE6-A84 exam dumps questions and practicing your skills, you can
increase your confidence and chances of passing the HPE6-A84 exam.
Features of Dumpsinfo’s products
Instant Download
Free Update in 3 Months
Money back guarantee
PDF and Software
24/7 Customer Support
Besides, Dumpsinfo also provides unlimited access. You can get all
Dumpsinfo files at lowest price.
Aruba Certified Network Security Expert Written Exam HPE6-A84 exam free
dumps questions are available below for you to study.
Full version: HPE6-A84 Exam Dumps Questions
1.You need to install a certificate on a standalone Aruba Mobility Controller (MC). The MC will need to
use the certificate for the Web UI and for implementing RadSec with Aruba ClearPass Policy
Manager. You have been given a certificate with these settings:
Subject: CN=mc41.site94.example.com
No SANs -
Issuer: CN=ca41.example.com -
EKUs: Server Authentication, Client Authentication
What issue does this certificate have for the purposes for which the certificate is intended?
A. It has conflicting EKUs.
B. It is issued by a private CA.
C. It specifies domain info in the CN field instead of the DC field.
D. It lacks a DNS SAN.
Answer: D
1 / 6

2.When would you implement BPDU protection on an AOS-CX switch port versus BPDU filtering?
A. Use BPDU protection on edge ports to protect against rogue devices when the switch implements
MSTP; use BPDU filtering to protect against rogue devices when the switch implements PVSTP+.
B. Use BPDU protection on edge ports to prevent rogue devices from connecting; use BPDU filtering
on inter-switch ports for specialized use cases.
C. Use BPDU protection on inter-switch ports to ensure that they are selected as root; use BPDU
filtering on edge ports to prevent rogue devices from connecting.
D. Use BPDU protection on edge ports to permanently lock out rogue devices; use BPDU filtering on
edge ports to temporarily lock out rogue devices.
Answer: B
3.A customer has an AOS 10-based solution, including Aruba APs. The customer wants to use Cloud
Auth to authenticate non-802.1X capable IoT devices.
What is a prerequisite for setting up the device role mappings?
A. Configuring a NetConductor-based fabric
B. Configuring Device Insight (client profile) tags in Central
C. Integrating Aruba ClearPass Policy Manager (CPPM) and Device Insight
D. Creating global role-to-role firewall policies in Central
Answer: B
4.Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba
Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Denied access to other 10.0.0.0/8 subnets
Permitted access to the Internet
Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only send
return traffic.
The exhibits below show the configuration for the role.
2 / 6
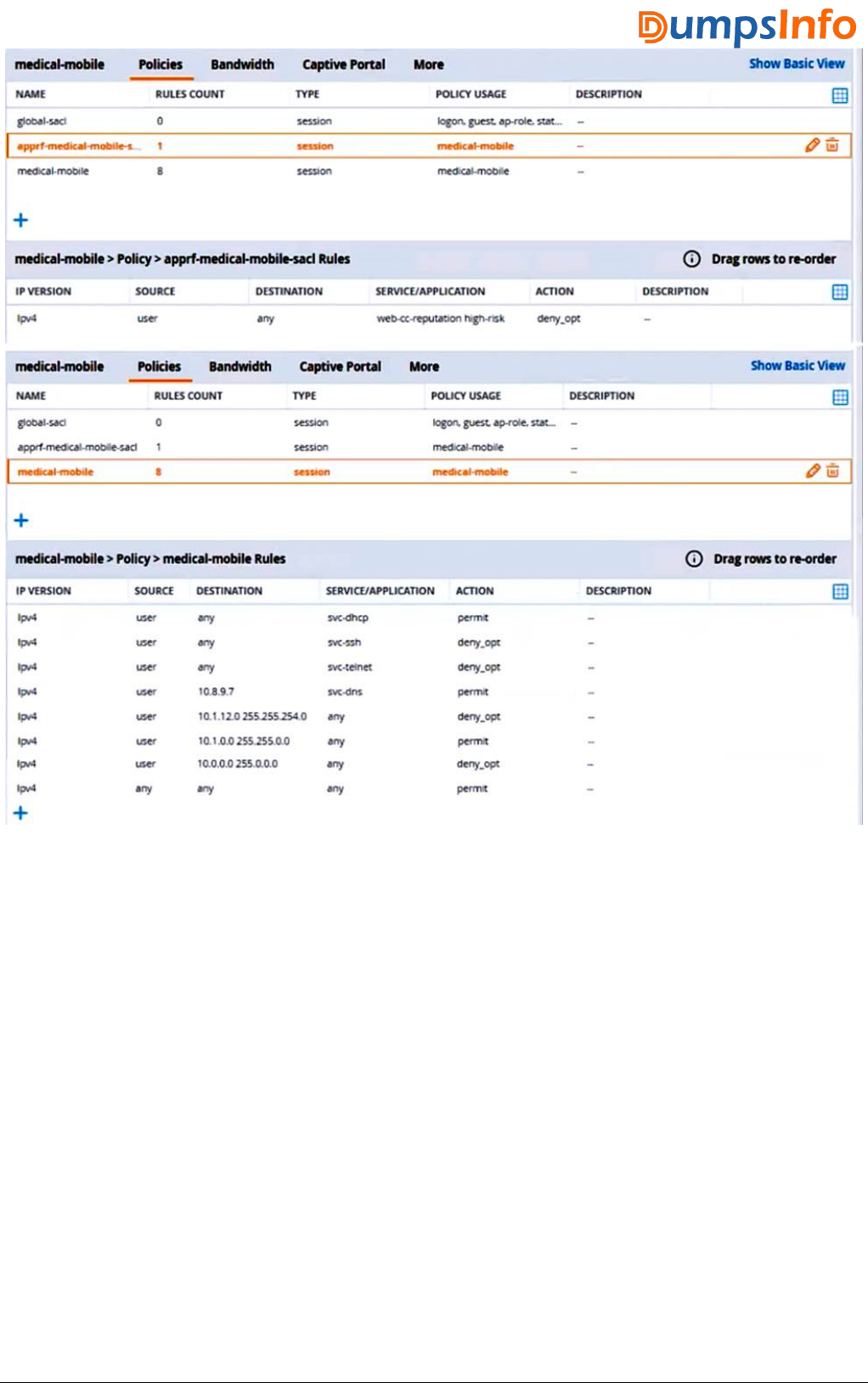
What setting not shown in the exhibit must you check to ensure that the requirements of the scenario
are met?
A. That denylisting is enabled globally on the MCs’ firewalls
B. That stateful handling of traffic is enabled globally on the MCs’ firewalls and on the medical-mobile
role
C. That AppRF and WebCC are enabled globally and on the medical-mobile role
D. That the MCs are assigned RF Protect licenses
Answer: C
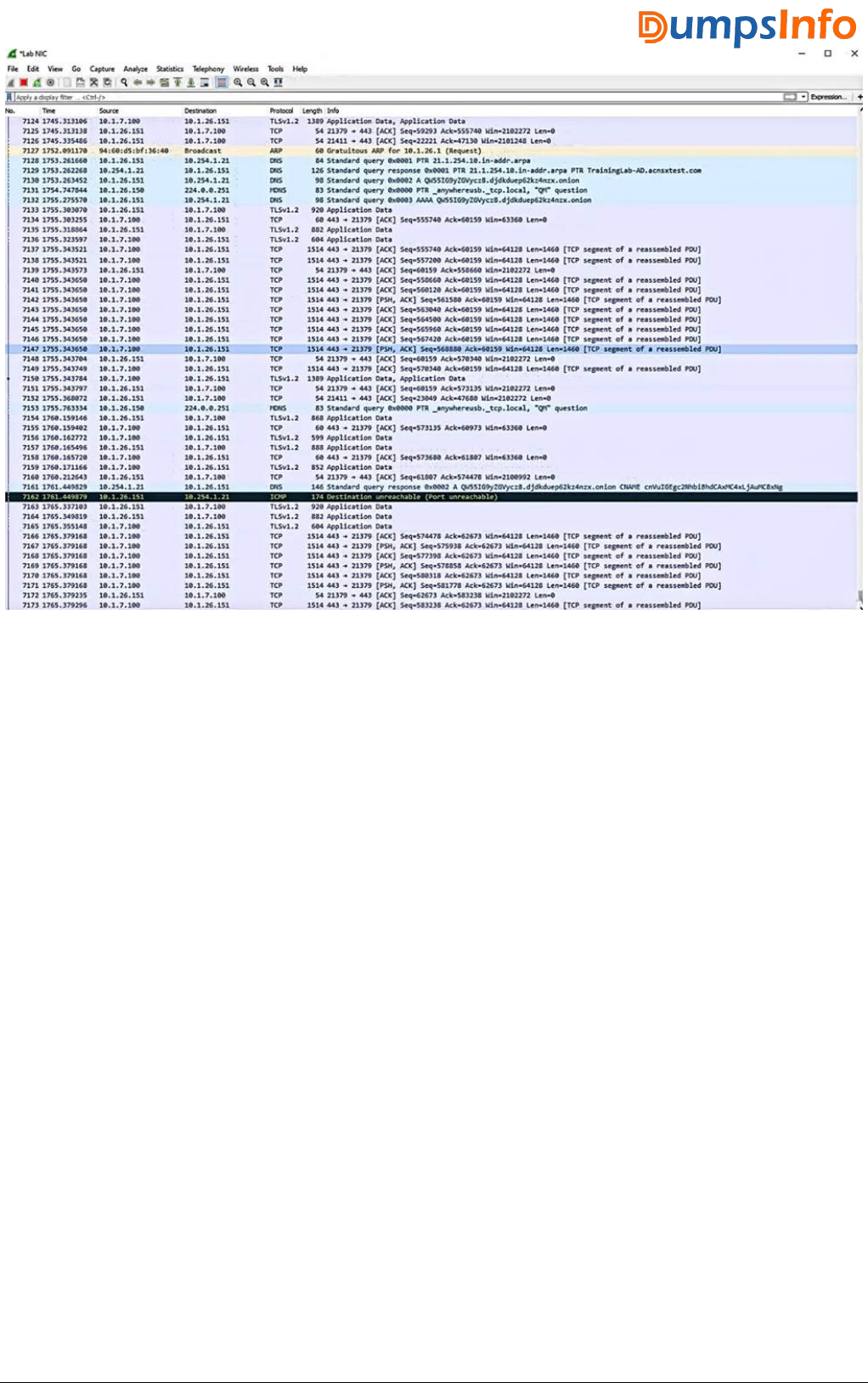
5.Refer to the exhibit.
3 / 6

What is one recommendation to make?
A. Let the RADIUS server configure VLANs on LAG 1 dynamically.
B. Use MDS instead of SHA1 for the NTP authentication key.
C. Encrypt the certificate in the TA-profile.
D. Create a control plane ACL to limit the sources that can access the switch with SSH.
Answer: D
7.1.You are designing an Aruba ClearPass Policy Manager (CPPM) solution for a customer. You
learn that the customer has a Palo Alto firewall that filters traffic between clients in the campus and
the data center.
Which integration can you suggest?
A. Sending Syslogs from the firewall to CPPM to signal CPPM to change the authentication status for
misbehaving clients
B. Importing clients’ MAC addresses to configure known clients for MAC authentication more quickly
C. Establishing a double layer of authentication at both the campus edge and the data center DMZ
D. Importing the firewall's rules to program downloadable user roles for AOS-CX switches more
quickly
Answer: A
8.What is a common characteristic of a beacon between a compromised device and a command and
control server?
A. Use of IPv6 addressing instead of IPv4 addressing
B. Lack of encryption
C. Use of less common protocols such as SNAP
D. Periodic transmission of small, identically sized packets
Answer: D
9.Refer to the scenario.
A customer has an AOS10 architecture that is managed by Aruba Central. Aruba infrastructure
devices authenticate clients to an Aruba ClearPass cluster.
In Aruba Central, you are examining network traffic flows on a wireless IoT device that is categorized
as “Raspberry Pi” clients. You see SSH traffic. You then check several more wireless IoT clients and
see that they are sending SSH also.
You want an easy way to communicate the information that an IoT client has used SSH to Aruba
ClearPass Policy Manager (CPPM).
What step should you take?
A. On CPPM create an Endpoint Context Server that points to the Central API.
B. On CPPM enable Device Insight integration.
C. On Central configure APs and gateways to use CPPM as the RADIUS accounting server.
D. On Central set up CPPM as a Webhook application.
Answer: D
Powered by TCPDF (www.tcpdf.org)
6 / 6
Text Material Preview
HPE6-A84 Aruba Certified Network Security Expert Written Exam exam dumps questions are the best material for you to test all the related HP exam topics. By using the HPE6-A84 exam dumps questions and practicing your skills, you can increase your confidence and chances of passing the HPE6-A84 exam. Features of Dumpsinfo’s products Instant Download Free Update in 3 Months Money back guarantee PDF and Software 24/7 Customer Support Besides, Dumpsinfo also provides unlimited access. You can get all Dumpsinfo files at lowest price. Aruba Certified Network Security Expert Written Exam HPE6-A84 exam free dumps questions are available below for you to study. Full version: HPE6-A84 Exam Dumps Questions 1.You need to install a certificate on a standalone Aruba Mobility Controller (MC). The MC will need to use the certificate for the Web UI and for implementing RadSec with Aruba ClearPass Policy Manager. You have been given a certificate with these settings: Subject: CN=mc41.site94.example.com No SANs - Issuer: CN=ca41.example.com - EKUs: Server Authentication, Client Authentication What issue does this certificate have for the purposes for which the certificate is intended? A. It has conflicting EKUs. B. It is issued by a private CA. C. It specifies domain info in the CN field instead of the DC field. D. It lacks a DNS SAN. Answer: D 1 / 6 https://www.dumpsinfo.com/unlimited-access/ https://www.dumpsinfo.com/exam/hpe6-a84 2.When would you implement BPDU protection on an AOS-CX switch port versus BPDU filtering? A. Use BPDU protection on edge ports to protect against rogue devices when the switch implements MSTP; use BPDU filtering to protect against rogue devices when the switch implements PVSTP+. B. Use BPDU protection on edge ports to prevent rogue devices from connecting; use BPDU filtering on inter-switch ports for specialized use cases. C. Use BPDU protection on inter-switch ports to ensure that they are selected as root; use BPDU filtering on edge ports to prevent rogue devices from connecting. D. Use BPDU protection on edge ports to permanently lock out rogue devices; use BPDU filtering on edge ports to temporarily lock out rogue devices. Answer: B 3.A customer has an AOS 10-based solution, including Aruba APs. The customer wants to use Cloud Auth to authenticate non-802.1X capable IoT devices. What is a prerequisite for setting up the device role mappings? A. Configuring a NetConductor-based fabric B. Configuring Device Insight (client profile) tags in Central C. Integrating Aruba ClearPass Policy Manager (CPPM) and Device Insight D. Creating global role-to-role firewall policies in Central Answer: B 4.Refer to the scenario. A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba Mobility Controllers (MCs): Permitted to receive IP addresses with DHCP Permitted access to DNS services from 10.8.9.7 and no other server Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22 Denied access to other 10.0.0.0/8 subnets Permitted access to the Internet Denied access to the WLAN for a period of time if they send any SSH traffic Denied access to the WLAN for a period of time if they send any Telnet traffic Denied access to all high-risk websites External devices should not be permitted to initiate sessions with “medical-mobile” clients, only send return traffic. The exhibits below show the configuration for the role. 2 / 6 https://www.dumpsinfo.com/ What setting not shown in the exhibit must you check to ensure that the requirements of the scenario are met? A. That denylisting is enabled globally on the MCs’ firewalls B. That stateful handling of traffic is enabled globally on the MCs’ firewalls and on the medical-mobile role C. That AppRF and WebCC are enabled globally and on the medical-mobile role D. That the MCs are assigned RF Protect licenses Answer: C 5.Refer to the exhibit. 3 / 6 https://www.dumpsinfo.com/ Which IP address should you record as a possibly compromised client? A. 10.1.26.151 B. 10.1.7.100 C. 10.1.26.1 D. 10.254.1.21 Answer: A 6.Refer to the scenario. A customer has asked you to review their AOS-CX switches for potential vulnerabilities. The configuration for these switches is shown below: 4 / 6 https://www.dumpsinfo.com/ 5 / 6 https://www.dumpsinfo.com/ What is one recommendation to make? A. Let the RADIUS server configure VLANs on LAG 1 dynamically. B. Use MDS instead of SHA1 for the NTP authentication key. C. Encrypt the certificate in the TA-profile. D. Create a control plane ACL to limit the sources that can access the switch with SSH. Answer: D 7.1.You are designing an Aruba ClearPass Policy Manager (CPPM) solution for a customer. You learn that the customer has a Palo Alto firewall that filters traffic between clients in the campus and the data center. Which integration can you suggest? A. Sending Syslogs from the firewall to CPPM to signal CPPM to change the authentication status for misbehaving clients B. Importing clients’ MAC addresses to configure known clients for MAC authentication more quickly C. Establishing a double layer of authentication at both the campus edge and the data center DMZ D. Importing the firewall's rules to program downloadable user roles for AOS-CX switches more quickly Answer: A 8.What is a common characteristic of a beacon between a compromised device and a command and control server? A. Use of IPv6 addressing instead of IPv4 addressing B. Lack of encryption C. Use of less common protocols such as SNAP D. Periodic transmission of small, identically sized packets Answer: D 9.Refer to the scenario. A customer has an AOS10 architecture that is managed by Aruba Central. Aruba infrastructure devices authenticate clients to an Aruba ClearPass cluster. In Aruba Central, you are examining network traffic flows on a wireless IoT device that is categorized as “Raspberry Pi” clients. You see SSH traffic. You then check several more wireless IoT clients and see that they are sending SSH also. You want an easy way to communicate the information that an IoT client has used SSH to Aruba ClearPass Policy Manager (CPPM). What step should you take? A. On CPPM create an Endpoint Context Server that points to the Central API. B. On CPPM enable Device Insight integration. C. On Central configure APs and gateways to use CPPM as the RADIUS accounting server. D. On Central set up CPPM as a Webhook application. Answer: D Powered by TCPDF (www.tcpdf.org) 6 / 6 https://www.dumpsinfo.com/ http://www.tcpdf.org